Overview
Continuous monitoring ensures your applications remain secure and compliant as new vulnerabilities are discovered and dependencies evolve. This guide demonstrates two approaches:- Dependency Track - Real-time vulnerability monitoring and risk management
- ORT Integration - Policy automation and compliance reporting
Dependency Track Integration
Dependency Track provides continuous monitoring of your Software Bill of Materials (SBOM) for vulnerabilities, license risks and policy violations.Prerequisites
Before you begin, ensure you have:- Completed CI/CD Integration to understand GitHub Actions workflows
- A running Dependency Track instance
- GitHub repository with Actions enabled
- SCANOSS API key
- Dependency Track API key (from Administration → Access Management → Teams → API Keys)
Configure GitHub Secrets
Navigate to your GitHub repository and add the required secrets: Settings → Secrets and variables → Actions Click New repository secret and add each of the following:| Secret Name | Description | Example |
|---|---|---|
DT_API_KEY | Dependency Track API key | abc123… |
DT_SERVER_URL | Dependency Track base URL | https://your-dependencytrack-url.com |
SCANOSS_API_KEY | SCANOSS API key | xyz789… |
Create Monitoring Workflow
Open your project in your IDE (for example, VS Code), then open the terminal in your project folder. If you haven’t already created the.github/workflows directory from the CI/CD Integration guide, create it now:
.github/workflows/scanoss-monitoring.yml:
- Event Triggers: Executes on pushes and pull requests for continuous validation
- Automatic Upload: Sends SBOM to Dependency Track for ongoing monitoring
- Policy Enforcement: Validates copyleft, undeclared components, and Dependency Track policies
Commit and Push Workflow
Open your terminal and execute these commands:Monitor Your Scan
- Go to your GitHub repository
- Click Actions tab
- Select your SCANOSS with Dependency Track workflow
- Monitor the execution
Review Pipeline Summary
After the workflow completes, navigate to the Summary page to review results.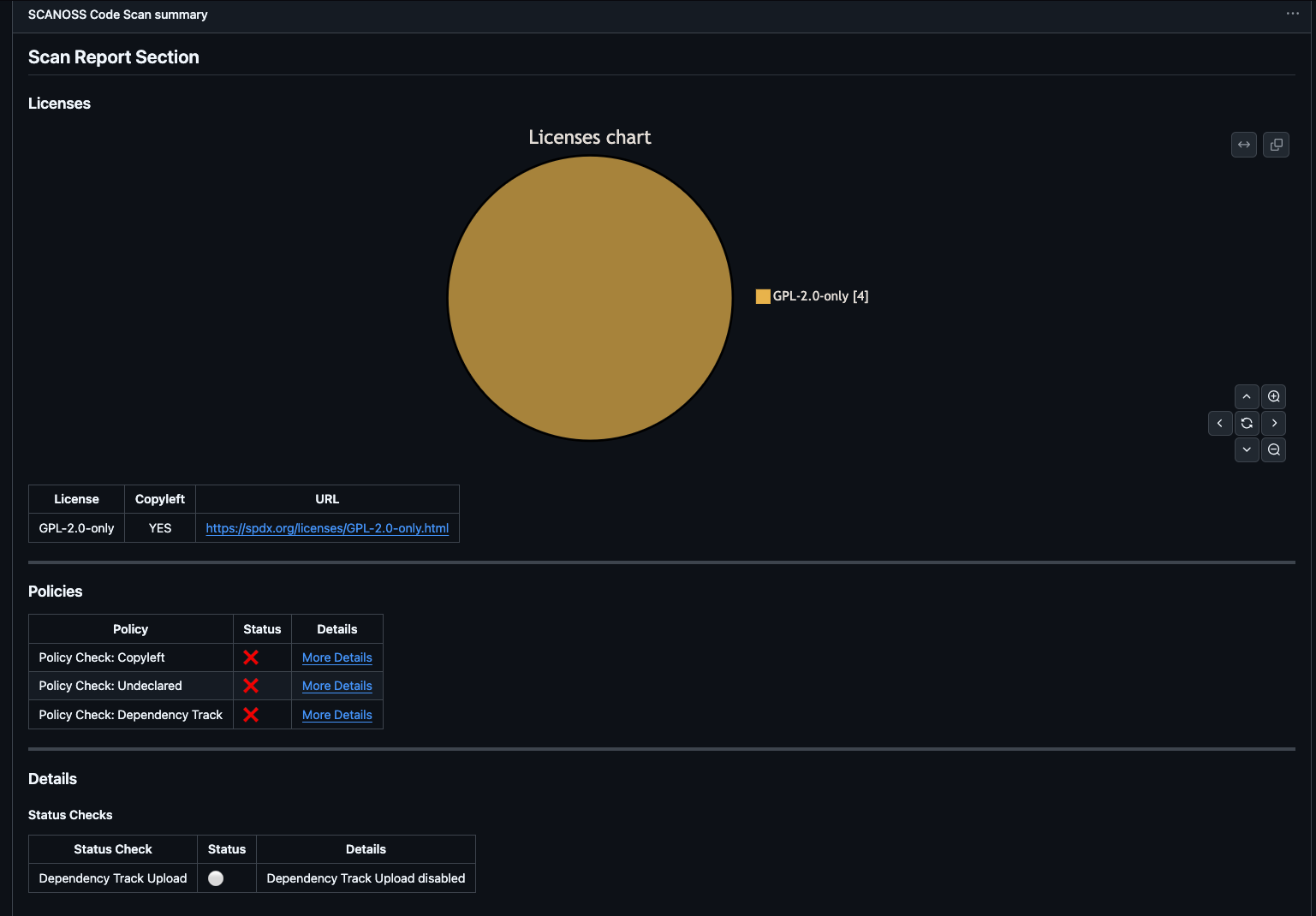
- Scan Report: License distribution pie chart and detailed license table
- Policies: Compliance check results (copyleft, undeclared, Dependency Track)
- Details: Upload status with direct link to Dependency Track project
- Artifacts: Downloadable reports, SBOMs, and policy results
Access Dependency Track Dashboard
Once the scan uploads to Dependency Track, access the full dashboard for deeper analysis. In the pipeline summary’s Details section, click the View Project link to open your project in Dependency Track.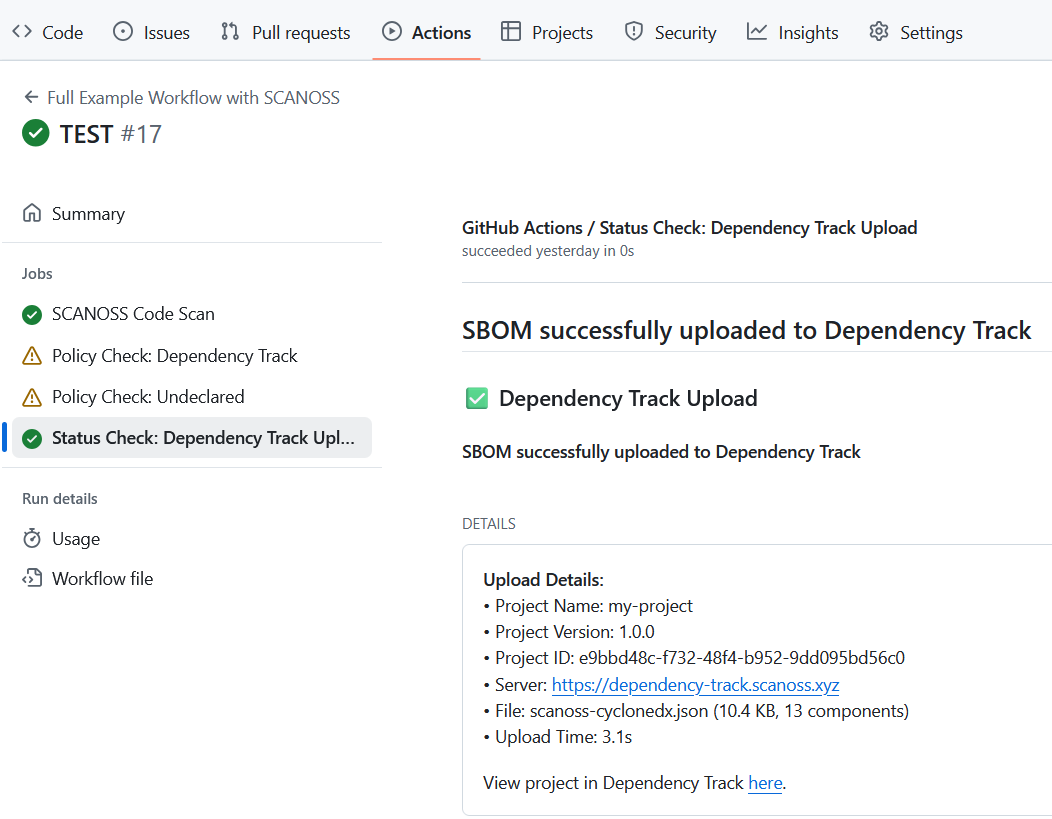
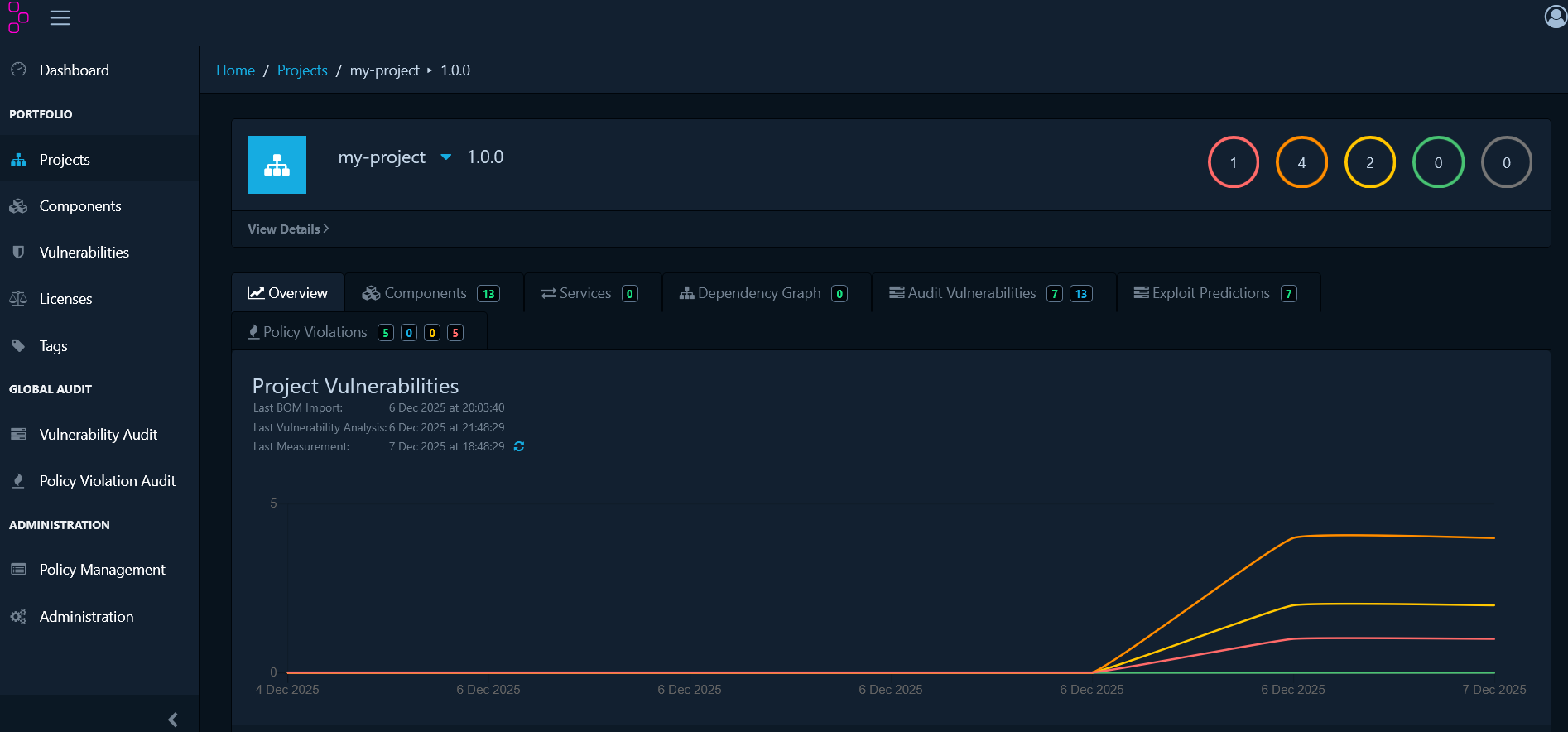
Explore Dashboard Sections
The Dependency Track dashboard provides several key views for managing your open-source dependencies:- Components: Complete inventory of detected components with their licenses, versions, and risk scores
- Dependency Graph: Visual representation of direct and transitive dependency relationships
- Audit Vulnerabilities: List of all components with known security vulnerabilities, organized by severity
Manage Vulnerabilities
Click on any vulnerability to open its details panel and assess its actual risk.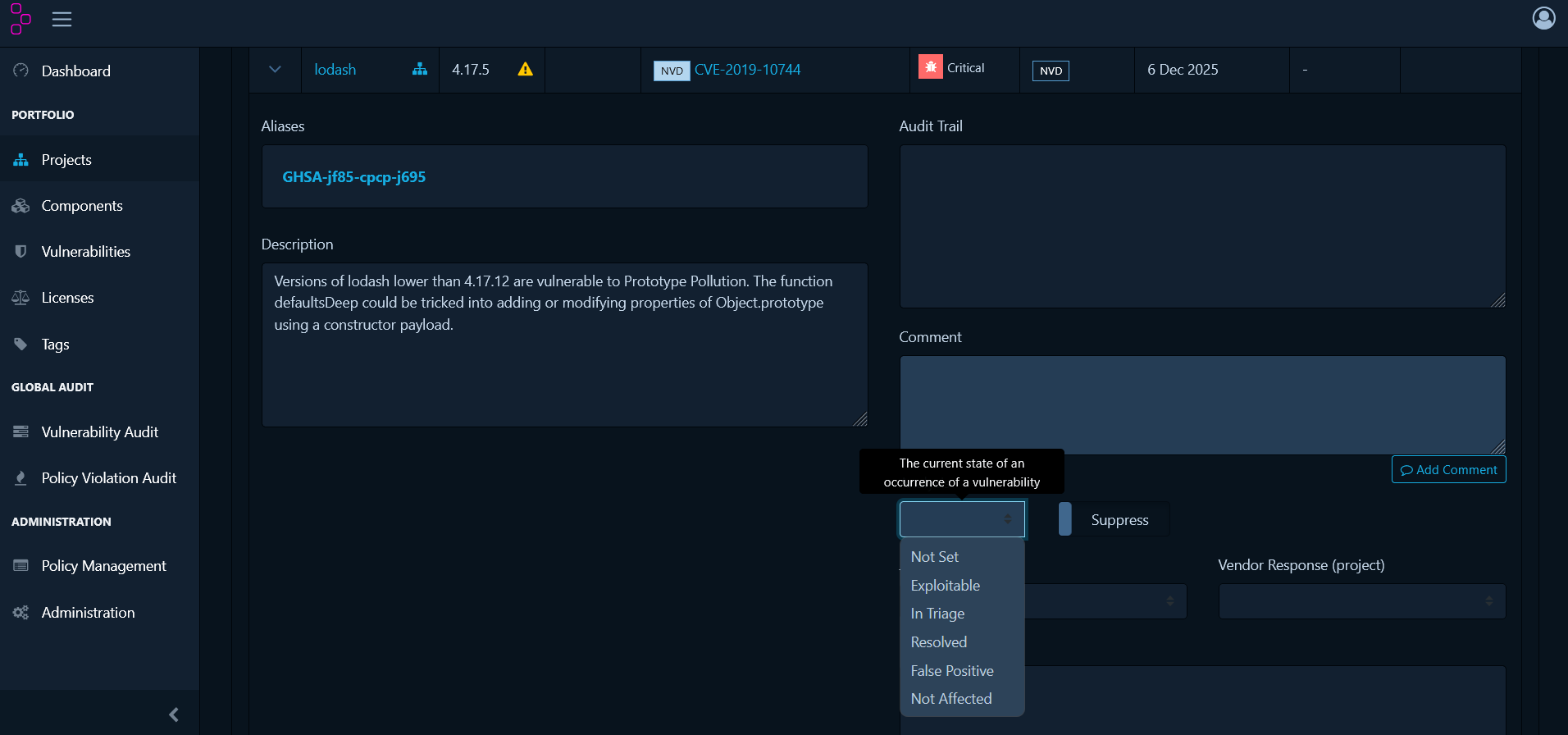
- Not Set - Default state requiring review
- Exploitable - Confirmed risk to your application
- In Triage - Currently under investigation
- False Positive - Doesn’t apply to your usage
- Not Affected - Your configuration isn’t vulnerable
- Resolved - Fixed (usually by upgrading)
- Click the vulnerability in the Audit Vulnerabilities tab
- Review the CVE details, affected versions and remediation advice
- Select an analysis state from the dropdown
- Add a comment explaining your decision
- Click Save
Define Organisational Policies
While vulnerability management handles security threats reactively, policy management takes a proactive approach by defining rules that automatically identify compliance issues. Navigate to Policy Management from the main menu to create policies.Create License Policies
Block Specific Licenses:- Click Create Policy
- Add a Condition and select License
- Choose the specific license to block (e.g., GPL-3.0)
- Set violation state to FAIL
- Save the policy
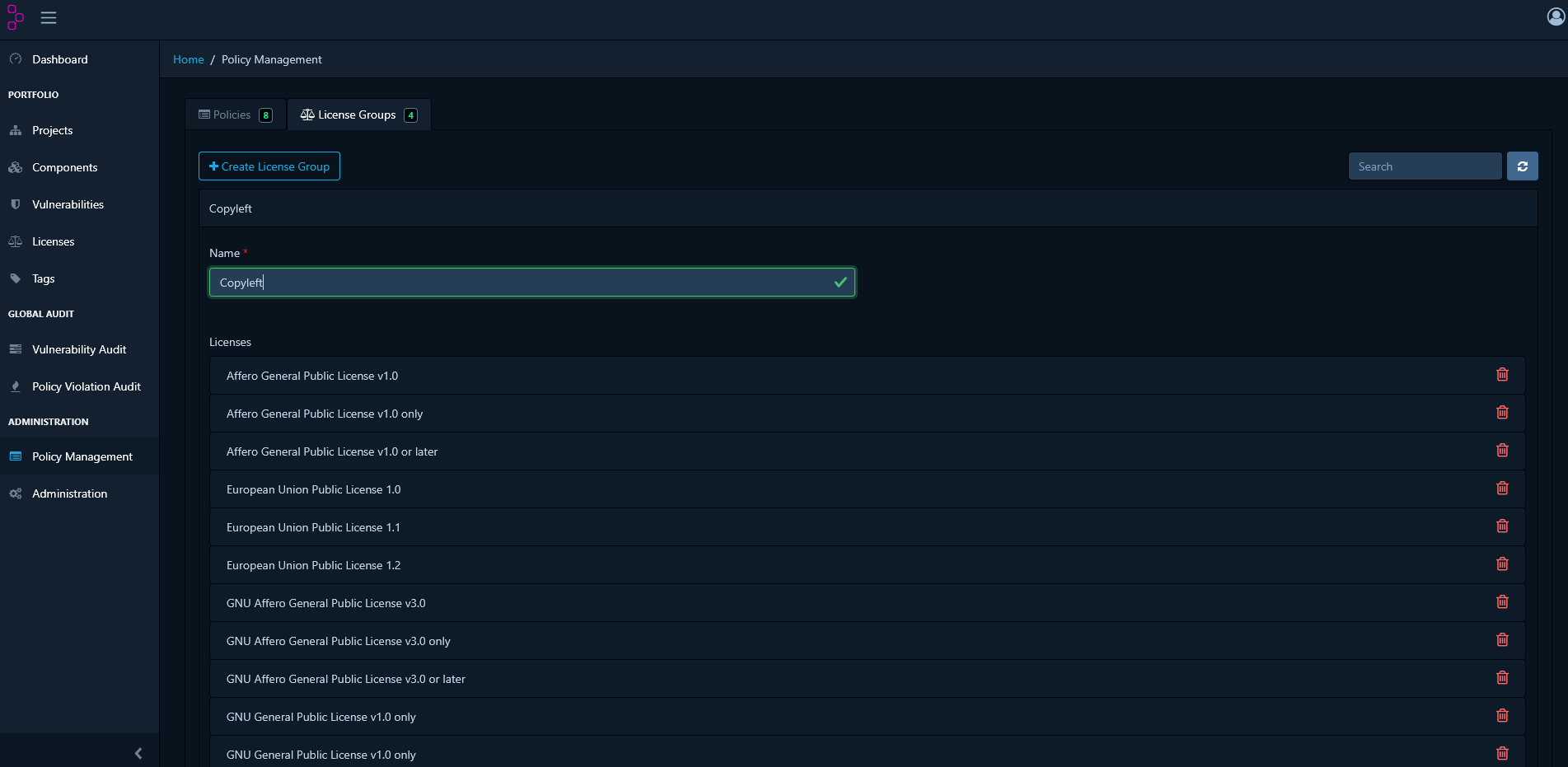
- Go to License Groups tab
- Click Create License Group
- Name it (e.g., “Copyleft Licenses”)
- Add licenses: GPL-2.0, GPL-3.0, AGPL-3.0
- Save the group
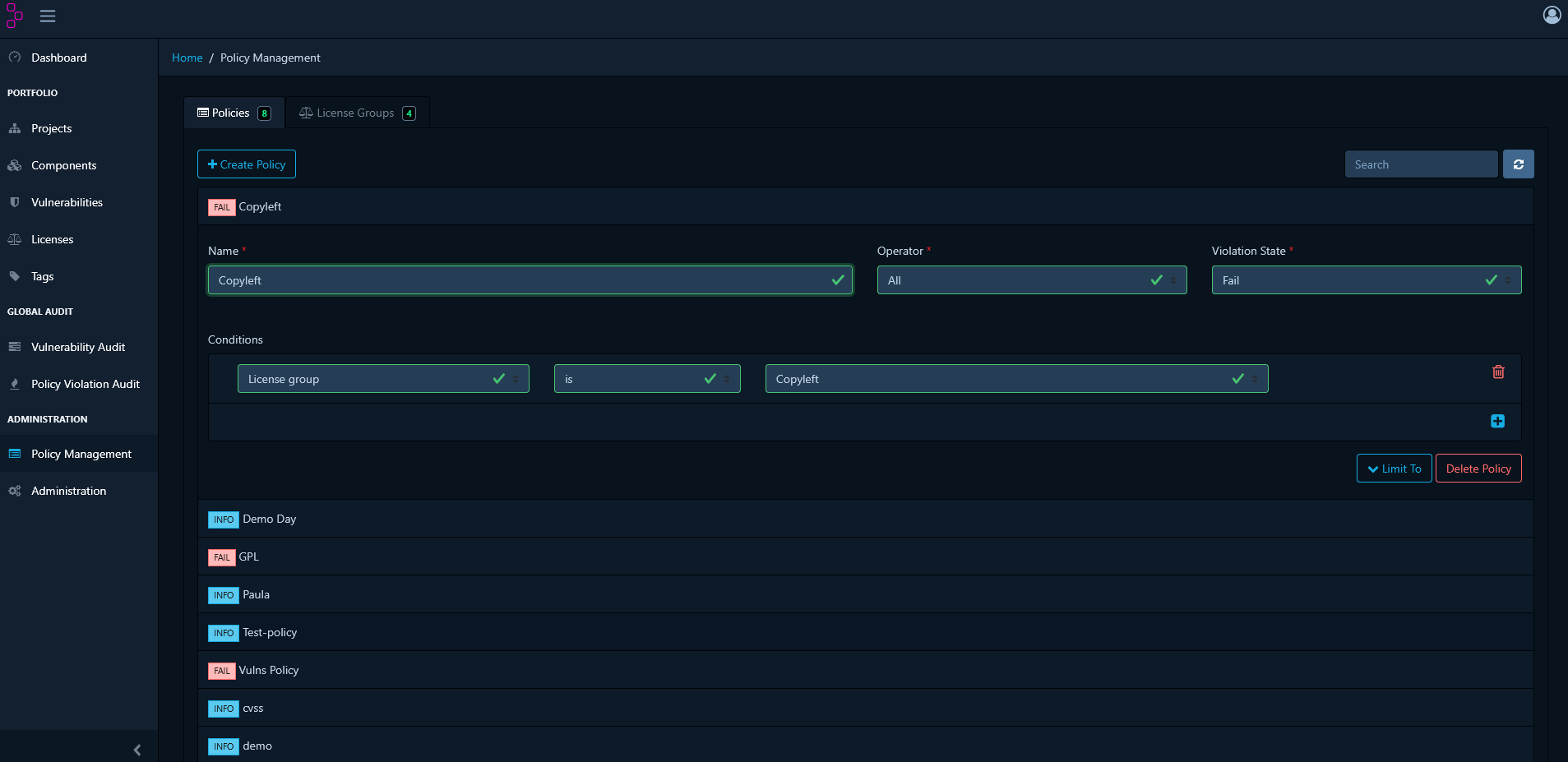
- Create Policy → Add Condition
- Select License Group
- Choose your license group
- Set violation state
- Save the policy
Create Vulnerability Policies
Flag High-Severity Vulnerabilities:- Click Create Policy
- Add a Condition and select Severity
- Select severity levels: CRITICAL, HIGH
- Set violation state to FAIL
- Save the policy
- Click Create Policy
- Add a Condition and select Vulnerability ID
- Enter CVE identifier (e.g., CVE-2024-1234)
- Set violation state to FAIL
- Save the policy
Create Component Age Policies
Flag outdated components that may lack security updates:- Click Create Policy
- Add a Condition and select Age
- Set operator to greater than
- Specify age threshold in days
- Set violation state to WARN
- Save the policy
Review Policy Violations
Navigate to your project’s Policy Violations tab to see all policy breaches: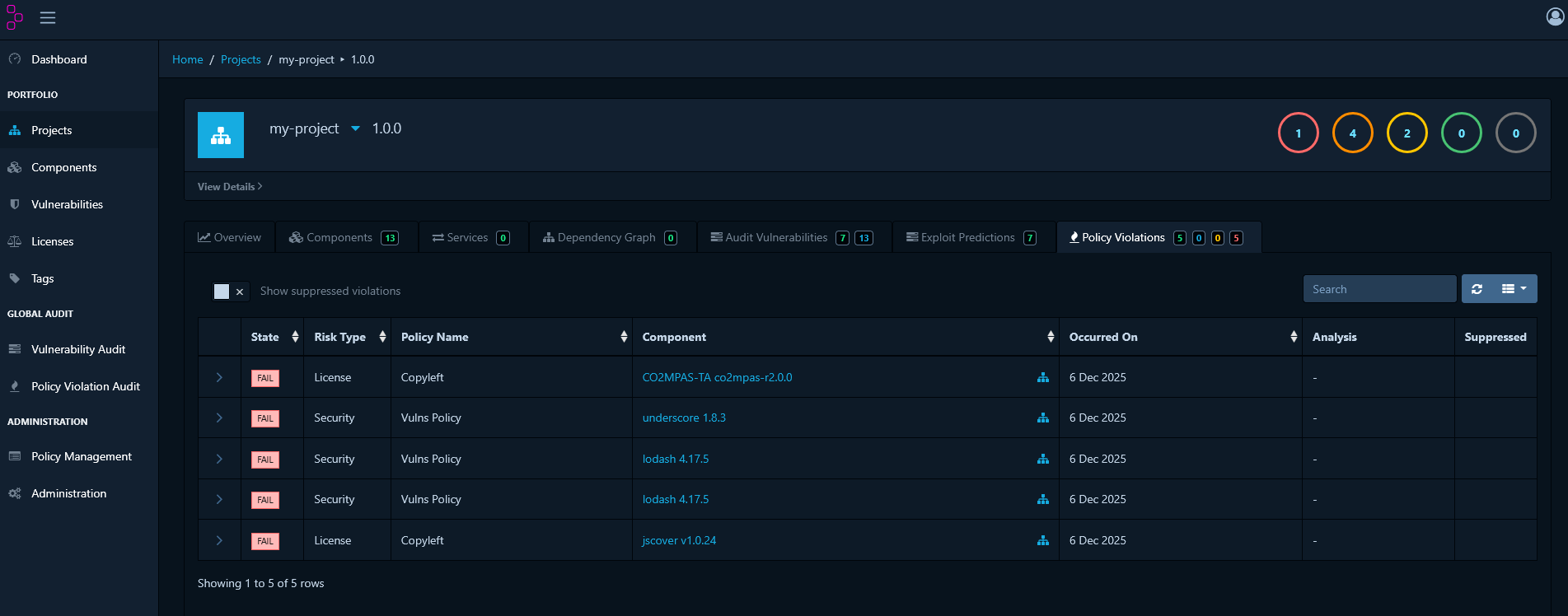
- INFO - Informational only, doesn’t block releases
- WARN - Requires review before release
- FAIL - Must be resolved before release
Triage Policy Violations
When a violation is technically accurate but acceptable in your context:- Navigate to Policy Violations tab
- Select the violation to triage
- Click Analysis
- Select an analysis state:
- Not Set - No decision made yet
- Approved - Reviewed and accepted as known exception
- Rejected - Not accepted, requires remediation
- Add a comment explaining the justification
- Save your decision
ORT Integration
OSS Review Toolkit (ORT) is an enterprise-grade FOSS policy automation and orchestration toolkit.Prerequisites
Before you begin, ensure you have:- Java: JDK 21 or later
- Git
- SCANOSS API key
- A shell environment:
- Windows: PowerShell, Command Prompt, or Git Bash
- macOS/Linux: Terminal (Bash/Zsh)
- A text editor of your choice (VS Code, Notepad++, nano, vim, etc.)
Install ORT
For Windows:- Variable name:
JAVA_OPTS - Variable value:
-Xmx8g
Configure SCANOSS Integration
Create the ORT configuration directory and file: For Windows:config.yml:
your-scanoss-api-key-here with your actual SCANOSS API key.
For macOS/Linux:
your-scanoss-api-key-here with your actual SCANOSS API key.
Analyse Your Project
Navigate to your project directory and run the analyser:Scan with SCANOSS
Run SCANOSS scanner through ORT:Define Policy Rules
Create custom compliance policies using ORT’s policy rules. For Windows:rules.kts: